Detailed difference OAuth 2.0 vs. OpenID are as many ways for cybersecurity attacks on data as there are, to secure it. From multi-way sign-in authentication or authorization to single sign-in, on-premises firewalls, the options are too many.
For developers and IT technologists, the alternative option of knowing to keep data and information security should be efficient. They also have to select the security protocol that professionals should use to keep federated identity safe.
The decision to choose one isn’t always a direct one. Many find it hard to differentiate between OAuth 2.0 and OpenID, each of which brings structure to the league of ‘Sign In’ process.
This blog brings clarity on what these standards mean, the comparison between OAuth 2.0 and OpenID, and the purposes for which enterprises should use them.
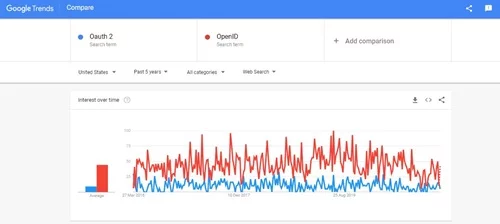
OAuth 2.0 vs. OpenID: Which is more popular?
From the above Google Trends screenshot, one can evaluate that OpenID is way ahead of OAuth 2.0 in terms of customer preferences.
OAuth 2.0 vs. OpenID: Difference Across Parameters
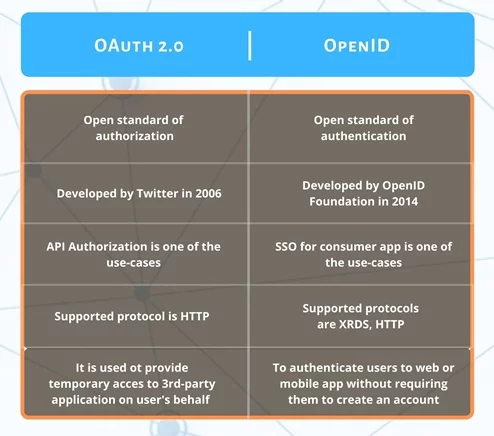
OAuth 2.0 (open authorization) is an open-for-all type of standard that ITEF created for a license for authorization. It allows natives and web applications to provide applications with ‘delegated authorization.’
Unlike other security shells that provide authentication, OAuth only AUTHORIZES devices, APIs, servers with access tokens are preferred over credentials as it works better than HTTP.
You would have seen one of a dialog box stating: Sign in with Google/Facebook. This is an application asking if it can access data on your behalf. This is OAuth.
The IETF developed the OAuth 2.0 protocol with Request for Comments (RFC) code 6749/4750. It enables more efficiency than the predecessor OAuth.
This kind of access requires Tokens, which represent the assigned right of access. That’s why apps or software get access without imitating the customer/client who manages the data.
How does OAuth 2.0 work?
An OAuth 2.0 Access Token interaction involves three participants: the client, e.g., us, the application (API), e.g., Hubspot, and the resource (service provider that has stored your privileged credentials), e.g., Google. The transaction begins once we have an objective to access the API.
- The app request permission:
The application or the API (application program interface) asks for interaction from the resource by providing the user’s verified identity on a 3rd-party app as proof. - The application requests Access Token:
After authorization has been authenticated, the resource grants an Access Token to the application without including usernames or passwords. - The application accesses resource:
Tokens come with access permission for the API. These permissions are called scopes, and each token will have an authorized scope for every API. The permitted app gets access to the resource only to the scope that it allows.
OpenID is an extra identity layer on top of the OAuth 2.0 security stack. It is an extended version of OAuth and allows for Federated Authentication.
The OpenID transaction procedure is the same as OAuth 2.0 authorization workflow. The significant difference is an ‘id-token’ instead of an access token that allows the user AUTHENTICATION.
We, as users, can have a lot of profiles on multiple websites. Hence it is difficult to remember the passwords of all profiles without having to forsake security.
But OpenID solves all these problems. With OpenID, one will need only a single username and password.
One has to create a single account with an email id and password in an IdP(provider), and that provider then confirms the identity to any websites they visit. Other than your provider, no other website can check/see your password.
How does OpenID work?
The user usually has an account created at OpenID provider, and he only has to prove his identification to the relying 3rd-party.
An OpenID can either be an Identifier or a URL.
- To get an OpenID, the customer/user should register herself on an OpenID provider. The user should prove her identity then, the user receives an OpenID link. So, the user should provide her OpenID when the relying application asks to enter. Most of the websites accept OpenID to sign in to their websites.
- Example of an OpenID: bobsmith2000.myopenid.com
You can sign in using this OpenID on any website.
- Authentication can be achieved via OpenID since each user can be recognized using an OpenID.
- So OpenID is decentralized. No one owns it as it is an open platform. User can create an account at an OpenID provider, and he needs to provides his OpenID credentials in each website whenever he/she logins.
Let’s take the example of Facebook and HubSpot again
- Federated Authentication
It is logging into HubSpot using your Facebook credentials. - Delegated Authorization
An external 3rd-party application can access resources. In this case, HubSpot is trying to get your Facebook friends to list to import it into their system.
In OAuth 2.0, at any time when a user wants to log in, he will be redirected to the login page, or a new pop-up page will appear for the authorization, unlike OpenID.
In OpenID, whenever a user wants to log in to a third-party app, he should enter his OpenID credentials to the 3rd-party applications.
After that, the 3rd-party app will redirect the user to the OpenID provider to confirm the login process. This is the main Detailed difference OAuth 2.0 vs. OpenID.
OAuth 2.0:
Suppose you’ve ever visited a new website and signed up(after agreeing to T&C). In that case, it will automatically find new contacts via Facebook or your mobile communications, then you’ve most likely used OAuth 2.0
This protocol provides secure delegated access. That means a 3rd-party app can access information from a server on behalf of the user without sharing their email id and password.
This is done by allowing the identity provider (IdP) to issue access tokens to third-party applications with the user’s approval. IdP is used by OpenID too.
OpenID:
If you’ve used your Google to log in to websites such as Spotify or to log in to an online shopping cart like Flipkart, then you’re familiar with this authentication option.
OpenID is an open protocol that many companies utilize to authenticate end-users. IdPs utilize this so that users can sign in directly to the OpenID.
It can then access other websites and apps without logging in or sharing their sign-in information.
Conclusion
There are many organizations that depend on software frameworks and security protocols like detailed difference OAuth 2.0 vs. OpenID to bring efficiency to the security of various native and web apps.
Any Cybersecurity or IT specialist should know how to protect their web or native applications with the help of these API integrations via Sign in authentication/authorization protocols.
As for the end-user, it is difficult to remember different log-in credentials for different websites and having one single authentication service at your disposal without having to forsake security is seen as a boon for many.
You May Also Like Read:
Everything you need to know about Decentralized Storage Systems
What is Supplementary Content (SC) and How Does it Help your Website?